High-end NAS manufacturer Asustor has confirmed that a Deadbolt ransomware attack is affecting its devices. The Asus subsidiary is the latest in a growing line of NAS providers to suffer from such security flaws, following a similar attack on Qnap devices earlier this year.
Hackers who have managed to encrypt the files of unsuspecting users are now holding Asustor owners hostage, seeking Bitcoin payment in return for an alleged decryption key intended to restore access.
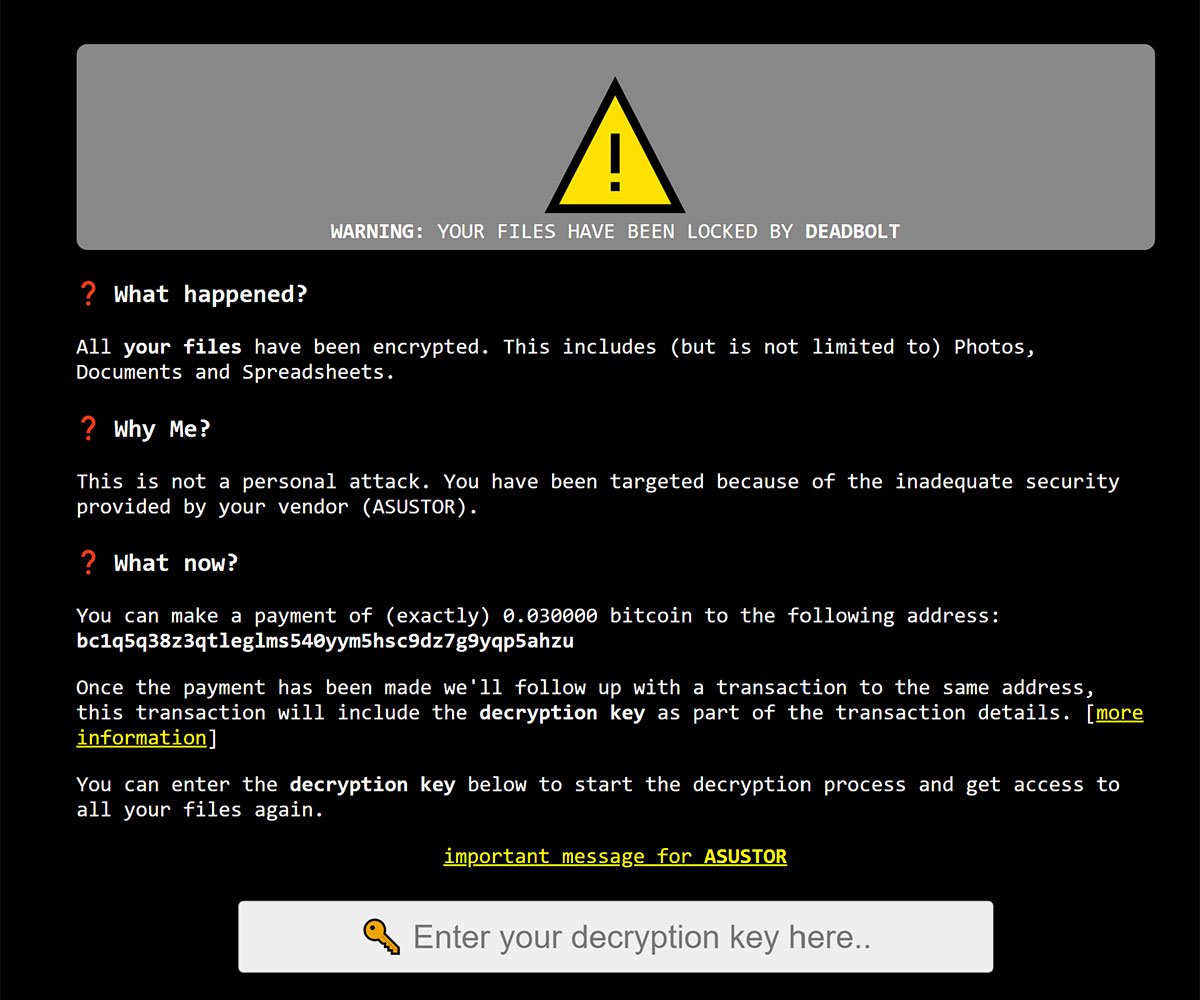
A warning that appears on affected NAS units has been shared by Reddit user Patrick12289, with the attacker claiming “you have been targeted because of the inadequate security provided by your vendor (Asustor).”
In response to the threat, Asustor has disabled its myasustor.com DDNS service and issued a series of precautionary measures for those who haven’t yet been affected:
- Change default ports, including the default NAS web access ports of 8000 and 8001 as well as remote web access ports of 80 and 443.
- Disable EZ Connect.
- Make an immediate backup.
- Turn off Terminal/SSH and SFTP services.
Those who have already fallen foul of the attack are advised to take more drastic action. “Unplug the Ethernet network cable,” says Asustor, before warning users “do not initialise your NAS as this will erase your data.”
The firm has made available a Deadbolt Ransomware Contact Form for affected users to get in touch directly, but the root cause and exactly which NAS models are susceptible remains unclear. Given the lack of clarity, many users are taking to a Reddit megathread which suspects that Plex media Server could be one potential vulnerability.
At the very least, this latest incident serves as a reminder to all NAS users; backup your important data and only allow access from outside your network if absolutely necessary.

